I tried to download the Facebook app for iPhone or iPad. Ask a Question Forced download of TrendMicro. Account Security. Has anyone else been forced to download a malware protection product called TrendMicro Housecall?
Figures of the year
- The share of spam in mail traffic came to 56.63%, down 1.68% against 2016.
- The biggest source of spam remains the US (13.21%).
- 40% of spam emails were less than 2 KB in size.
- The most common malware family found in mail traffic was Trojan-Downloader.JS.Sload
- The Anti-Phishing system was triggered 246,231,645 times.
- 9% of unique users encountered phishing
Global events in spam
Spam emails that mention the hottest topics in the world news agenda are a permanent feature of junk traffic. This trend has been observed for several years and is unlikely to change any time soon. Natural disasters in 2017 (hurricanes Irma and Harvey, the earthquake in Mexico) were a gift to fraudsters. “Nigerian” scammers bombarded mailboxes with messages asking for assistance in obtaining the inheritance of deceased relatives and donations for disaster victims, etc. Natural disasters were also a common theme in advertising spam and emails offering jobs and loans.
In 2017 spammers made frequent mention of natural disasters
Sporting events are another favorite topic of spammers. The most popular — and most mentioned in fake giveaway messages — are major soccer competitions and the Olympics. Back in 2016 we picked up emails citing the FIFA 2018 World Cup, and the following year their number increased, with the format and content unchanged. Typically, such emails say that during such-and-such lottery, supposedly held by a well-known organization, the recipient was randomly selected among a million others as the winner of a huge cash prize. Besides money, scammers sometimes promise tickets to competitions. The details are usually outlined in file attachments using official competition and sponsor logos.
“Winning” the lottery can be timed to major sporting events
The “Nigerian” scammers often refer to famous figures. Presidents and other political VIPs are especially in demand. In 2017, one of the most popular figures for fraudsters was US President Donald Trump.
We predict that in 2018 scammers will continue to pay close attention to world events and famous figures so as not to let slip the chance to squeeze ever more money and personal info out of gullible victims.
Cryptocurrencies in spam
Throughout the year we wrote that cryptocurrencies had gained a foothold in advertising spam and fraudulent mailings: all the numerous “Earn from home” schemes, financial pyramids, fake lottery wins, and phishing scams, etc., seem to have been updated and given a cryptocurrency makeover. Let’s try to systematize the various types of cryptocurrency-related spam.
Seminars
As major conferences and seminars are held on blockchain technology, spammers are making increasing use of this topic for their own purposes. The seminars advertised in their mailings don’t overload users with technical details, but promise to teach them how to extract eye-watering profits from cryptocurrencies. Such mailings are relatives of “traditional” spam on the topic “How to make a killing on the stock exchange.”
Financial fraud
A specific type of cryptocurrency fraud relates to fake “cloud mining” services. Such services hire out the mining power of their own specialized data centers. Fake sites offer similar services, but on paying up, the user receives neither mining power nor their money back. The crypto version of the classic pyramid scam warrants a special mention: the user “receives” mining income until they enlist other victims (for which there is also a reward). But sooner or later the cash flow stops, and the original investment is not repaid.
Fake “cloud mining” services offer enticing rewards
Sites masquerading as cryptocurrency trading platforms operate in a similar manner. The crucial difference between them and real exchanges is that money can only be invested, not withdrawn. Revenue usually “grows” very quickly, stimulating the user to invest more funds.
On fake cryptocurrency exchanges, experience really isn’t necessary
More subtle are binary options brokers (and their fake counterparts). We covered them in a previous report.
Another type of cryptocurrency fraud is fake services offering to exchange one currency for another, or convert it into “real” money. Scammers lure victims with favorable exchange rates, and then make off with the cash.
The “currency exchange desk” simply pockets the money for itself
Spam is very often used for this kind of fraud because it gives what all scammers crave — anonymity.
Other types of fraud
More traditional types of fraud, such as fake lottery wins, started using bitcoin bait:
Malware
CryptoLocker, whose creators demanded payment in bitcoin, was found in spam far less often than in 2016. That said, we encountered various modifications of Locky, Cerber, Rack, and other ransomware. At the same time, new capabilities such as stealing passwords from cryptocurrency wallets and mining were added to spam-distributed malware.
What’s more, a host of malware was distributed in spam under the guise of bitcoin mining tools or trading instructions.
Facebook Forcing Malware Download 2017 Free
The attached document was detected as HEUR:Exploit.RTF.Generic
Address databases
Targeted address databases advertised through spam were updated with the email addresses of cryptocurrency users, putting the address owners at risk of a targeted attack (for example, phishing as mentioned above).
Like other hot global issues, cryptocurrency is set be a recurring theme in spam for a very long time to come. And given the juicy rewards on offer, 2018 can expect to see growth in both fraudulent and phishing “cryptocurrency” spam.
Spamming by ethnicity
As we all know, spam peddles everything from potency-enhancing drugs to fake goods by well-known brands — it’s an international phenomenon that knows no geographic boundaries. However, 2017 caught the eye for some more localized spam content.
China and manufacturing
Back in 2016, we wrote about the Chinese habit of using spam to market goods internationally. Nothing changed in 2017: More and more Chinese companies are offering their products in this way.
India and IT
Whereas the Chinese are keen to sell goods on the international market, spam from India is more likely to offer IT services: SEO, web design, mobile apps, and much more:
Russia and seminars
Russian spam is written in, yes, Russian — and is therefore aimed at the domestic market. It too advertises goods and services, but more striking is the range of seminars and training on offer:
America and targeted business spam
In the US, the law governing the distribution of advertising messages operates on the opt-out principle. Accordingly, users can be sent messages until they explicitly unsubscribe from the mailing list in question, for which a link must be provided. The CAN-SPAM Act stipulates many other legal requirements for mailings. The legislation demands that the message body match the subject in terms of topic, there be no automatic collection of addresses, the advertiser’s physical address appear in the text, and much more.
Using the opt-out principle, many small, and sometimes not-so-small, companies send out promotional materials to people who have not subscribed to them. A legal gray area arises from the fact that even if spam-mailing companies are physically located in the US, the emails are distributed worldwide, and most countries operate an opt-in policy, requiring the prior consent of recipients. In other words, some countries at the legislative level consider mailshots to be spam.
A trait of business spam is its very narrow targeting of companies operating in specific areas. Oftentimes, mailings are not directed to the company as a whole, but to people with certain job titles.
Malware and the corporate sector
The number of malicious spam messages in 2017 fell 1.6-fold against 2016. Kaspersky Lab clients registered a total of 145,820,119 triggers of Mail Anti-Virus throughout 2017.
Number of Mail Anti-Virus triggers among Kaspersky Lab clients in 2017
This drop is due to the unstable operation of the Necurs botnet: it mediated the spread of far fewer mailings, and in Q1 2017 was completely idle. Malicious mailshots sent via Necurs were short, not personalized. They were used to try to install cryptolockers from the Locky family on recipients’ computers.
In general, 2017 was marked by a large cluster of malicious, but well-crafted emails, containing fragments of business correspondence matching the company profile, plus the full details of the organizations in whose name they had been sent.
Emails containing malicious objects detected as Backdoor.Java.Adwind.cu
The messages were not mass-distributed, but most likely targeted. Based on the target domain names, it can be assumed that the attackers were primarily interested in the corporate sector, while the tactic of citing previous messages of the addressee suggests in some cases a Business Email Compromise-type attack.
An email containing a malicious object detected as Trojan-PSW.Win32.Fareit.dnak
Malware downloaded onto the victim computer most often had functions for collecting detailed information about the system and its settings (as well as passwords, keystrokes, etc.), and then transferring this data to a remote server. For information about potential targets and perpetrators of such attacks, see our article.
Phishing
Phishing pages migrate to HTTPS
Sites have been moving to HTTPS in increasing numbers, and not just legitimate resources. If a year ago a top tip for users was “check that pages requesting personal data are secure,” today a certificate does not guarantee safety: anyone or anything could be behind it.
Where do scammers get certificates? For domains created specifically for fraudulent purposes, attackers most likely use free 90-day certificates from Let’s Encrypt and Comodo, two certificate authorities. Getting hold of one is simplicity itself.
A phishing site with a free 90-day certificate issued by Let’s Encrypt
What’s more, phishing pages are often located on hacked sites that already have the necessary certificates.
A phishing page located on a hacked site with HTTPS
Scammers also make use of free web hosting with an SSL certificate:
On the topic of free hosting sites, it should be noted that attackers often use services that do not closely monitor user-posted content. It is not uncommon for phishing content to be placed on free hosting sites of well-known companies: this reduces the risk of the page being blacklisted, since it is located on a reputable domain with a high-profile name and a good SSL certificate. And although such services are pro-active in the fight against illegitimate content, phishing pages on their domains are found fairly often.
A phishing page located on the Google Sites service redirecting users to a third-party resource where payment system data is requested
Phishing pages located on the Force.com Sites service
Punycode encoding
Another important rule is to always check the spelling of the domain name, a task made more difficult due to the active use by phishers of Punycode encoding, which helps mask phishing domain names under the domains of well-known brands. Web browsers use Punycode to display Unicode characters in the address bar, but if all the characters in the domain name belong to the character set for one language, the browser displays them not in Punycode format, but in the specified language. Scammers select characters similar or identical to ones in Latin script, and use them to create domain names that resemble those of well-known companies.
The technique is not new, but caused a real stir this year, especially after an article by Chinese researcher Xudong Zheng. As an example, he created a domain with a name that in the address bar was indistinguishable from Apple’s domain. Phishers aren’t always able to find identical symbols, but the results are still look pretty convincing.
Examples of domains displayed in Punycode in browser address bars
Besides the external similarity to the original domain, such domains are more difficult to detect by keywords.
Fake cryptocurrency wallets
Fraudsters are always up to speed on the latest trends, brands, and news hooks. The hype around cryptocurrencies in 2017 reached such a crescendo that even those far removed from the virtual world were snapping up bitcoin, whatever it was.
As a result, cryptocurrency wallets were a very attractive target for phishers. Proof of this is the large number of phishing pages spoofing cryptocurrency wallets. We encountered Coinbase, BitGo, and Xapo, to name just a few. One of the leaders by number of spoofs is blockchain.info.
Examples of phishing pages mimicking user sign-in to popular cryptocurrency wallets
Scammers also spoof popular cryptocurrency services in an attempt to get users to hand over money under the guise of lucrative investments.
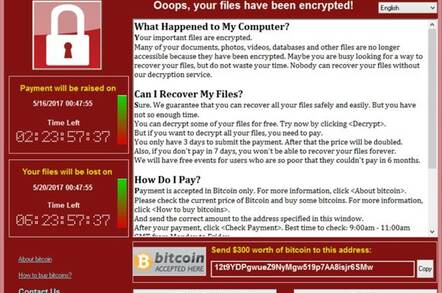
Facebook Forcing Malware Download 2017 Full
Social media fraud
In Q2, social networks were hit by a wave of air ticket giveaways. Scammers set up websites under famous airline brands that were supposedly raffling off tickets. After completing a short survey, the user was redirected to a resource created by the attackers. This could be an infected site, a phishing page prompting to install malware under the guise of a browser update, or a page spreading malicious content, etc.
Examples of Facebook posts with links to various scamming domains
The scheme is not new, but the distribution mechanism in this case is innovative: in winning a “prize,” users themselves shared unsafe content in social media.
For some domains in the scheme, visitor activity statistics were available, according to which just one of the sites was visited by more than 2,500 users worldwide in the space of an hour:
In Q3, scammers shifted their attention to WhatsApp and extended their assortment of fake prizes.
Fake giveaways that began their odyssey in social media migrated to WhatsApp, and the range of prizes expanded
Fake viruses
Cybercriminals often don’t even bother to write malware, using instead fake virus notifications supposedly from common operating systems. Such messages often appear as pop-up ads or as the result of the user being passed through a redirect chain. This might happen after completing a survey, as in the scheme described above.
The scammers’ primary aim is to intimidate and coerce users into calling a “technical support” number where they are offered solutions to disinfect their computer — not free of charge, of course.
Examples of pages showing fake system infection messages
It’s not only Windows users in the firing line. Scammers are targeting Apple products, too.
Example of a page showing a fake system infection message

Under the same guise, cybercrooks also distribute insecure software.
Example of a page showing a fake system infection message and prompting to download a file
Tax refunds
Another eternal topic is tax returns and tax refunds. Public trust in government sites plays an important role in the success of phishing operations in this segment. Exploiting features of the taxation system in different countries, scammers carry out successful attacks in the US, France, Canada, Ireland, and elsewhere.
Examples of phishing pages using the names of tax authorities in different countries
The new iPhone
The release of the new version of the popular smartphone also attracted scammers, with attempts to redirect users to phishing pages mimicking Apple sites growing 1.5-fold in September, when the latest iteration of the flagship series went on sale.
Number of Anti-Phishing triggers on user computers caused by attempts to redirect to phishing sites using the Apple brand, 2017
The launch of Apple’s new smartphone inspired a host of fraudulent schemes, including fake giveaways, sales of counterfeit devices, and classic phishing scams mentioning the brand.
Statistics: spam
Proportion of spam in email traffic
The share of spam in email traffic in 2017 fell by 1.68% to 56.63%.
Proportion of spam in global email traffic, 2017
The lowest share (52.67%) was recorded in December 2017. The highest (59.56%) belonged to September.
Sources of spam by country
Facebook Forcing Malware Download 2017 Windows 7
In 2017, the US remained the biggest source of spam (13.21%). A 6.59% hike in spam distribution pushed China up to second place (11.25%). Vietnam took bronze (9.85%).
India slipped from third to fourth (7.02%), showing a 3.13% decline in its share of spam. Next came Germany (5.66%, +2.45%) and Russia (5.40%, +1.87%).
In the seventh place was Brazil (3.97%, -0.04%). And in ninth, France (3.71%, -0.32%). Italy rounds off the Top 10 with a score of 1.86%, up 0.62% against 2016.
Spam email size
In 2017, the share of very small emails (up to 2 KB) in spam again dropped sharply, averaging 43.40%, which is 18.76% less than in 2016. The proportion of emails ranging in size from 2 to 5 KB amounted to 5.08%, another significant change.
Spam emails by size, 2017
There was further growth in the share of emails between 5 and 10 KB (9.14%, +2.99%), 10 and 20 KB (16.26%, +1.79%), and 20 and 50 KB (21.23%, +11.15%). Overall, spam in 2017 did not buck the trend of fewer very small emails and rising numbers of average size emails (5-50 KB).
Malicious attachments in email
Malware families
In 2017, the most common malware family in email traffic was Trojan-Downloader.JS.Sload — a set of JS scripts that download and run other malicious programs on the victim computer, usually encryptors.
Runner-up was last year’s leader Trojan-Downloader.JS.Agent — the typical member of this malware family is an obfuscated JS that uses ADODB.Stream technology to download and run DLL, EXE, and PDF files.
Third place went to the Backdoor.Java.Qrat family — a cross-platform multi-functional backdoor written in Java and sold in the Darknet under the umbrella of Malware-as-a-Service (MaaS). It is generally distributed by email in the form of JAR attachments.
The Worm.Win32.WBVB family took fourth place. It includes executable files written in Visual Basic 6 (both in P-Code mode and Native mode) that are untrusted in KSN.
Trojan-PSW.Win32.Fareit completes the Top 5. This malware family is designed to steal data, such as the credentials of FTP clients installed on infected computers, cloud-storage credentials, browser cookies, and email passwords. Fareit Trojans send the information collected to the attackers’ server. Some members of the family can download and run other malware.
In sixth position was the Trojan-Downloader.MSWord.Agent family. This malware takes the form of a DOC file with an embedded macro written in Visual Basic for Applications (VBA) that runs when the document is opened. The macro downloads another malicious file from the attackers’ site and runs it on the user’s computer.
In seventh is Trojan.PDF.Badur, which poses as a PDF document containing a link to a potentially dangerous site.
Eighth place was occupied by the Trojan-Downloader.VBS.Agent family — a set of VBS scripts that use ADODB.Stream technology to download ZIP archives and run malware extracted from them.
Trojan.WinLNK.Agent found itself in ninth position. Members of this malware family have the extension .lnk and contain links for downloading malicious files or a path for running another malicious executable file.
One more family of Trojan loaders, Trojan.Win32.VBKrypt, props up the Top 10.
Countries targeted by malicious mailshots
In 2017, Germany (16.25%, +2.12%) held on to top spot. China (12.10%) climbed from third to second, adding 4.78% for the year. Russia (6.87%, +1.27%) rounds off the Top 3.
Countries targeted by malicious mailshots, 2017
Further down come Japan (5.32%, -2.27%), Britain (5.04%, -0.13%), Italy (4.89%, -0.55%), and Brazil (4.22%, -0.77%).
Eighth place is taken by Vietnam (2.71%, +0.81%). And ninth by France (2.42%, -1.15%). The Top 10 is rounded off by the UAE (2.34%, +0.82%).
Statistics: phishing
In 2017, the Anti-Phishing system was triggered 246,231,645 times on computers of Kaspersky Lab users as a result of phishing redirection attempts. That is 91,273,748 more than in 2016. In all, 15.9% of our users were targeted by phishers.
Organizations under attack
The rating of organizations targeted by phishing attacks is based on the triggering of the heuristic component in the Anti-Phishing system on user computers. This component detects all instances when the user tries to follow a link in an email or on the Internet to a phishing page in the event that such links have yet to be added to Kaspersky Lab’s databases.
Organizations under attack by category
The lion’s share of heuristic component triggers in 2017 went to pages that mentioned banking organizations (27%, +1.24%). Second place in the rating is the Payment systems category (15.87%, +4.32%), followed by Online stores (10.95%, +0.78%).
Distribution of organizations subject to phishing attacks by category, 2017.
See our financial report for more details about phishing in the financial sector.
Top 3 organizations under attack from phishers
As before, the trend in mass phishing is still to use the most popular brands. By doing so, scammers significantly increase the likelihood of a successful attack. The Top 3 is made of organizations whose names were most often used by phishers (according to the heuristic statistics for triggers on user computers):
| 7.97% | |
| Microsoft Corporation | 5.57% |
| PayPal | 4.50% |
The geography of attacks
Countries by percentage of attacked users
As in the previous year, Brazil had the highest percentage of attacked unique users out of the total number of users in the country, seeing its score increase by 1.41% to 29.02%.
Percentage of users on whose computers the Anti-Phishing system was triggered out of all Kaspersky Lab users in the country, 2017
Top 10 countries by percentage of attacked users
| Brazil | 29.02% |
| Australia | 22.51% |
| China | 19.23% |
| Qatar | 18.45% |
| Bolivia | 18.38% |
| Albania | 17.95% |
| New Zealand | 17.85% |
| Portugal | 16.76% |
| Angola | 16.45% |
| Russia | 16.43% |
Top 10 countries by percentage of attacked users
The number of attacked users also increased in Australia — by 2.43% to 22.5%. Next come China (19.23%), where the share of attacked users fell by 3.61%, and Qatar (14.45%).
Results
The number of malicious spam messages in 2017 fell 1.6-fold against 2016. This drop is due to the unstable operation of the Necurs botnet, which mediated the spread of far fewer mailings.
In 2018, spammers and phishers will continue to closely monitor world events and famous figures so as not to miss any opportunity to extract money and personal info from their unsuspecting targets. We can expect mailings to refer to the Winter Olympic Games, the FIFA World Cup, the presidential elections in Russia, and other events. What’s more, the first few months of the year are likely to experience a wave of phishing pages and mailshots exploiting the topic of tax refunds, since in many countries April is tax payment month. The theme of cryptocurrency will be popping up in spam for a very long time to come. And given the juicy rewards on offer, 2018 can expect to see growth in both fraudulent and phishing “cryptocurrency” spam.
The number of phishing sites using SSL certificates will surely continue to grow. As will the use of different domain name obfuscation methods.
Protecting millions from malware with cleanup tools
UPDATE: We no longer use Kaspersky software for this malware scanning feature. (11/3/2017)
Malware Download Free
Keeping links to malware off of our platform is a core function of our Security team. To really stick it to the fraudsters, we go beyond one-off, 'whack-a-mole' removals to systematically combat malicious activity and do away with whole clusters of bad links at a time. This strategy works well, but to make an even greater impact, we begin a few steps earlier and help fix compromised computers when they connect to Facebook. We use a combination of signals to help find infections and get the malware off of your computer for good, even if the malware isn't actively spreading spam or harmful links.
For the past year, we've been working with anti-malware companies like ESET, F-Secure, and Trend Micro to offer free malware cleanup software to people who use Facebook. Thanks to the collaboration with these companies, in the past three months we have helped clean up more than 2 million people's computers that we detected were infected with malware when they connected to Facebook. In these cases, we present a cleanup tool that runs in the background while you continue using Facebook, and you get a notification when the scan is done to show you what it found.